Building Secure Products: konplan’s Approach to Cybersecurity in Development
Cybersecurity has become an essential aspect of product development in recent years. Industries across the board have established cybersecurity frameworks that span the entire product lifecycle. These frameworks are based on a vast array of guidance documents from organizations like IEC, FDA, and NIST, with significant overlap among them. For instance, medical applications are covered by standards such as IEC 81001-5-1, while industrial applications should adhere to the IEC 62443 series. Even specialized areas like wireless connectivity have dedicated standards such as EN 18031-1.
The recently adopted EU Cyber Resilience Act (CRA) impacts the industry. The act enforces new or updated QMS processes in companies (e.g. for development, incident and response management, etc.). The CRA also mandates specific requirements for product design, implementation, and labeling based on the product’s classification and criticality. New harmonized standards are also expected in the coming years. MedTech products are exempt from the law, as there are already cybersecurity regulations for MedTech. In contrast, industrial automation and control systems (IACS) are affected by the CRA, and the IEC 62443 family will most likely be updated as well. However, the CRA does not reinvent the wheel, so existing security principles and approaches will still be valid for the new CRA in one way or another.
konplan often senses that uncertainty prevails in all industries with regard to cybersecurity and that it is unclear what is really required by the regulators. Throughout the last few years, konplan has gained experience in various projects and understands meanwhile which cybersecurity aspects need to be emphasized and what methodologies work to deliver tangible results.
Cybersecurity as Integral Part of the Development Process
Regulations in MedTech (FDA, MDR) prescribe the required development activities from security requirements engineering, secure architectural design, verification and validation and post market activities as well as the expected deliverables. Furthermore, the system use cases must also integrate and support the misuse cases: incident detection, response, cyber resilience and recovery.
Cybersecurity aspects not only focus on the actual product, but also on the development infrastructure such as protection of the software code repositories, check-in of code, pipeline, deployment, etc.
Different Approaches in industry
Independent of the industries, cybersecurity is all about protecting the assets of a system against attacks (and incorrect use) such that the objectives “confidentiality,” “integrity” and “availability” (CIA) of the system can be maintained along its lifecycle. It is a shared responsibility between the manufacturer (device) and the operator (context). Nowadays, the question is not “if” there will be a cyber-attack, but rather “when” it will be and how to deal with it.
The risk of a cyber-attack is a combination of likelihood, exploitability and the actual impact (i.e. violating the CIA triad). In MedTech, the likelihood of an attack is usually discarded in the risk assessment. The exploitability describes “how much effort would be needed” for a successful attack. Cyber-attacks exploit vulnerabilities to intrude into the system and such an exploit can be easy or more complex depending on the vulnerability.
Whereas the threat modeling and cybersecurity risk analysis are pivotal in MedTech, the industrial cybersecurity standard rather uses a checklist approach with predefined criteria that must be satisfied for a specific security level: In a first step, the context and the intended use of the system is assessed and the required so-called “security levels” for the system and zones/segments are identified with the help of an initial risk assessment. The security levels are somewhat “fuzzy” defined in the standard IEC 62443, though. Afterwards, the checklists for the system and components apply and the manufacturer must ensure that the required security levels are achieved for the individual components. The checklists consist of specific criteria such as authentication, authorization, encryption, access management, etc.
Nevertheless, both approaches – risk analysis-based and checklist-based – will lead to the same or very similar results. Besides, the type of effective countermeasures against cyber-attacks are repetitive and often the same independent of the product.
From an industry point of view, it would be a relief if the standardization bodies would agree on a single harmonized approach.
Software Design and Implementation
In a system, there can be vulnerabilities “by design” as well as by faulty implementation. Potential vulnerabilities by design are identified and assessed based on the system architecture and data flows by using threat modeling. The identified threats are evaluated in the cybersecurity risk analysis and effective countermeasures must be defined and integrated in the design.
Vulnerabilities by implementation can be identified by using secure coding guidelines, static code analysis, unit testing and reviews to the own code base and by vulnerability scanning of the third-party components based on the software bill of material (SBOM). The vulnerability scanner searches publicly accessible databases for known vulnerability of the components used in the system. A discovered vulnerability with a unique CVE ID is scored using the CVSS that provides a rating between 0…10. Potential vulnerabilities by implementation need to be monitored throughout the product life since a product that is considered secure today might turn insecure tomorrow if a vulnerability is discovered in a software component.
Apart from the regular verification, a system needs to be fuzz and penetration tested, i.e. to provide evidence for the effectiveness of security countermeasures (security requirements) including maintaining the CIA triad, incident detection and cyber resilience.
konplan’s Cybersecurity Approach in Development
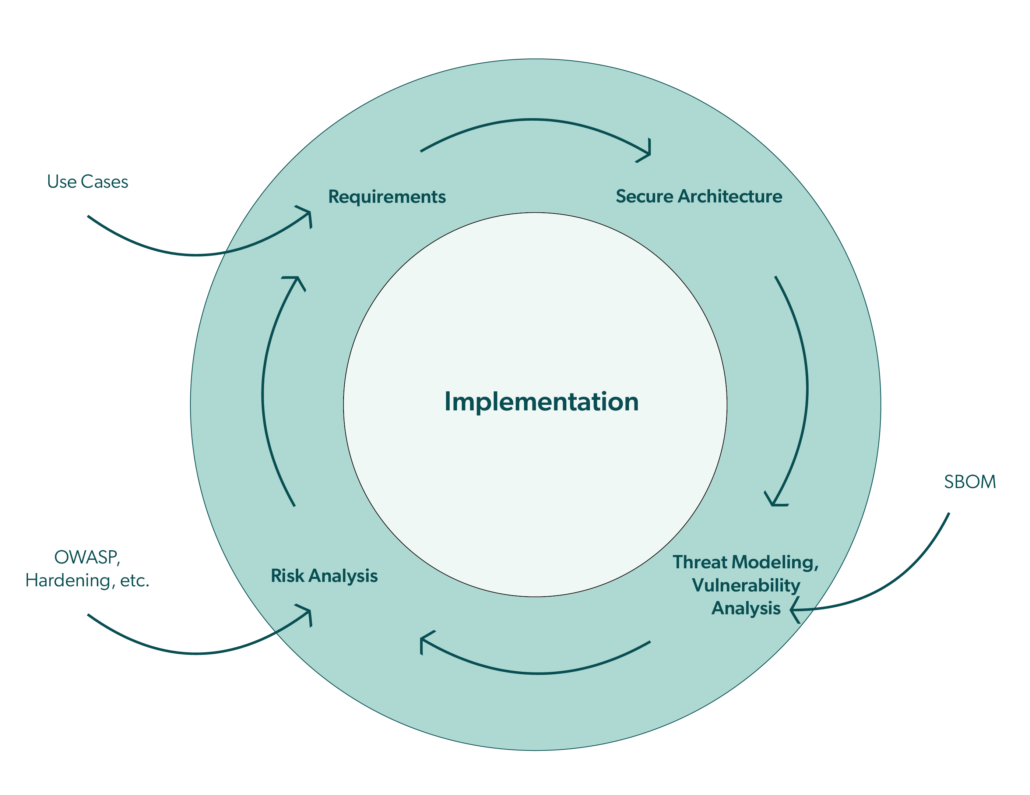
konplan considers cybersecurity as an integral part of the development process in compliance with the regulations. In a development project, we emphasis the following topics to obtain a secure holistic product solution:
- Elaboration of the various use cases for the intended product in its contexts together with our customer by considering different viewpoints. An important viewpoint is cybersecurity, which often has not only technical but also organizational impacts on the use cases.
- Iterative development of the system architecture along with the assets as well as with system and security requirements in a top-down approach. The architecture also reflects the Defense-in-Depth concept.
- Applying threat modeling (typically using the STRIDE method) in a bottom-up approach to gain systematic insights for potential threats. We usually keep the threat model at an abstract level to allow an effective identification of threats and potential countermeasures. In MedTech, threat modeling is used as input to the cybersecurity risk analysis and this in turn is an input to the safety risk analysis.
- Utilization of OWASP and databases such as CWE as further inputs to the cybersecurity risk analysis.
- Assessment of the technical system design and assets for overarching cybersecurity risks, e.g. with the help of the attack tree method. These types of risks are product- and context-specific.
- Detailing of the security requirements and design decisions in design specifications that can be used as a kind of “cookbook” for the actual implementation.
Eventually, a well-documented “security by design” is delivered in accordance with regulatory needs, such as security requirements and controls, secure architectural design considering defense-in-depth, security use cases, cybersecurity risk analysis and implementation guidelines.
This information will also be used as a basis for the fuzz testing of the product and the planning of the penetration testing. Eventually, a successful penetration test paves the way towards the product market launch.
konplan can provide support for cybersecurity to customers in the medical and the industrial sectors in all phases of a product’s life:
- Secure product and software design in compliance with regulations
- Secure software development and implementation, e.g. secure coding, static code analysis, vulnerability scanning integrated in the CI/CD pipeline, etc.
- Cybersecurity consulting in product development
- Support in establishing a secure development environment
- Security assessment of existing designs
- Monitoring and maintaining security of product designs, e.g. SBOM analysis
________________________________________________________________________
Author:
Ivo Locher, Program Manager
We are here for you – send us your request!
Developing together! We put your ideas into practice and accompany your projects until they are ready for the market. Get in touch with our experts now.

